First I want to discuss a little about proxychain with you. Those who do not know this is about, must not skip anything. In the matter of privacy & security, it should not be followed knowing half of anything. And those who know, I hope you will know better by reading this article.
Anonymity vs Privacy
Anonymity means a person’s true identity is not revealed or unknown. Nobody knows about that particular person. If anybody try to find out them, they can’t reach them easily.
Privacy means an individual hides his personal information or control other’s access to their personal information. Privacy can be changed according to an individual’s choice. Privacy is a person’s right.
There are many ethical issues are raised by increased anonymity-
1. Number of hackers increased- they take benefit of anonymity and make use of other’s personal information for their own benefit with the help of internet. For example- online money frauds.
2. Antisocial groups use this to spread terror among people and influence people to join them.
3. Negative people use anonymity to spread negativity in the society; they use abusive language on social media platforms.
Lets Talk about it first. Proxychain is a system where your IP will access the site once or twice with 3 or more nodes or proxy servers. Like the one you see in the movie what hacker does to hide his IP address. Police tries to find the hacker but his location shows many places at a time and the police can't pin point his address. Its kind of similar to that.
It's a little complex to understand. So I gave it with the diagram below -
Lets Talk about it first. Proxychain is a system where your IP will access the site once or twice with 3 or more nodes or proxy servers. Like the one you see in the movie what hacker does to hide his IP address. Police tries to find the hacker but his location shows many places at a time and the police can't pin point his address. Its kind of similar to that.
It's a little complex to understand. So I gave it with the diagram below -

After so much security and how to track that IP Adress? Maybe the security services which track them have that much technology. So you would think 100 times before doing something bad. You can survive without doing bad deeds. And yes it is definitely an educational tutorial. For Web Security and privacy. Everything has its ups and downs. I, we, none of the group or jhotpotinfo are responsible for the negative use of it.
I hope you all know how a vpn works or how to tunnel network. But if you want a post to explain it in a very good way, just tell me in the comment box I will post about that.
This is the concept of ProxyChain. I think everyone understands. I don't think it's right to do something like a robot in Linux or anywhere else without fully understanding the concept. Now I will show you how to use the proxychain program / tool.
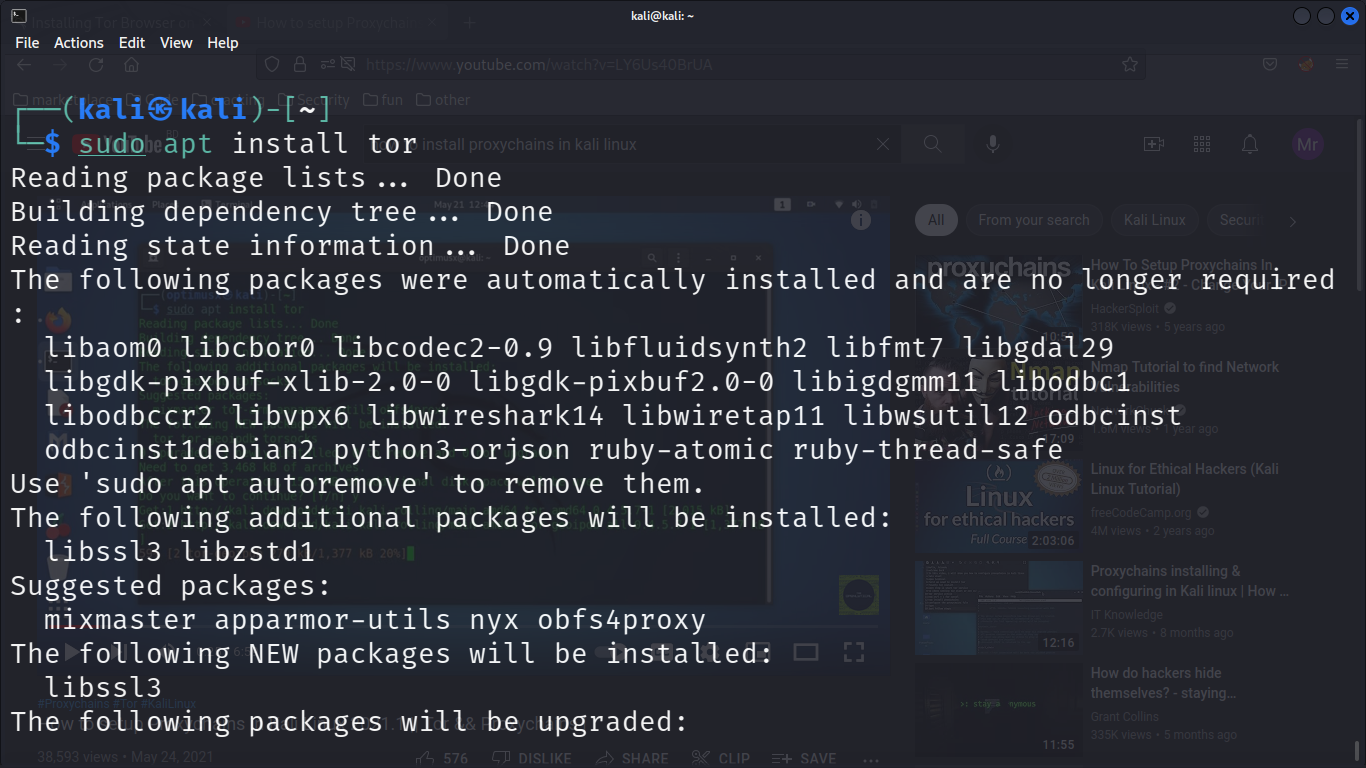
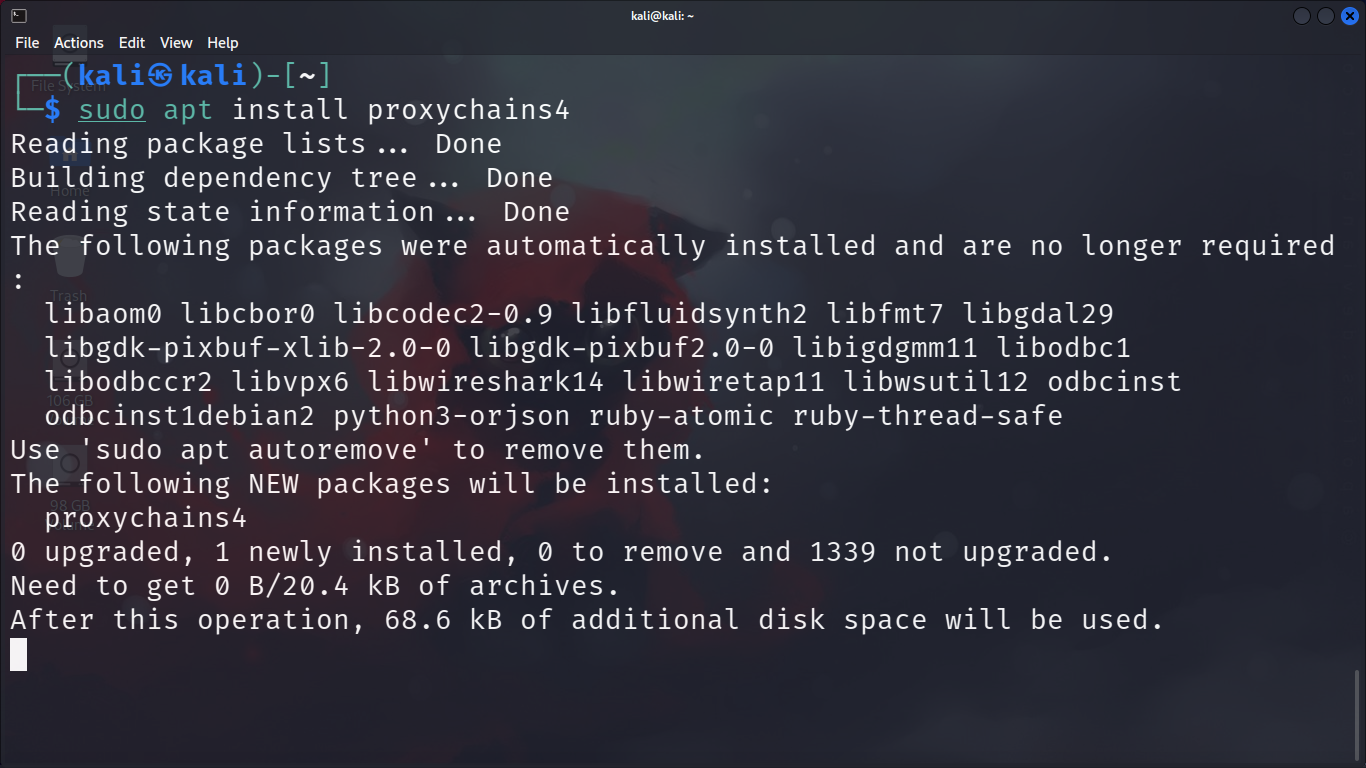
We need "Tor service" for Proxychain to work. You will need a linux operating system for this to work.
This is the concept of ProxyChain. I think everyone understands. I don't think it's right to do something like a robot in Linux or anywhere else without fully understanding the concept. Now I will show you how to use the proxychain program / tool.
We need "Tor service" for Proxychain to work. You will need a linux operating system for this to work.
Tags:
PC Hacks